The Essentials Of DevSecOps: A Detailed Guide Software Development

In recent years, the term “DevSecOps” has likely been used often, and for good reason. Nowadays, development companies usually compete every minute to bring out the next innovative app due to the increasing competition in the software industry and the evolving nature of consumer expectations. In the quest for speed, security is often overlooked.
Inevitably, many businesses have learned the hard way that compromising security when rapidly marketing a product comes at a high cost.
Are you familiar with the most recent episode of Solarwinds? In this attack, hackers gained access to the computers of the well-known IT Company Solarwinds, breaking security measures and inserting harmful code. The attack went undetected for months, allowing the threat actors to eavesdrop on Solarwinds’ customers and obtain their private information.
Releasing software with security flaws is a negative business strategy that can result in harsh regulatory fines, legal damages, and serious reputational harm from well-publicized breaches. The main idea behind DevSecOps is that security must be deeply rooted in the software development process. This blog addresses the DevSecOps method, its fundamental ideas, and how to execute it in your company.
What is DevSecOps?
DevSecOps is a method of integrating security testing at every stage of the software development process. It involves tools and processes that boost collaboration between developers, security experts, and operation teams to build effective and secure software. DevSecOps brings cultural transformation that makes security a collective duty for everyone building software.
What does DevSecOps stand for?
DevSecOps, an extension of the DevOps practice, stands for development, security, and operations. Each term describes the diverse roles and responsibilities of software teams during the development of software applications.
-
Development
Development refers to planning, coding, building, and testing the application.
-
Security
Security means leading security earlier in the software development cycle. For instance, programmers make sure that the code is free of security exposures, and security experts test the software additionally before its company release.
-
Operations
The operations team issues, monitors, and fixes any problems that come from the software.
DevSecOps Market Size
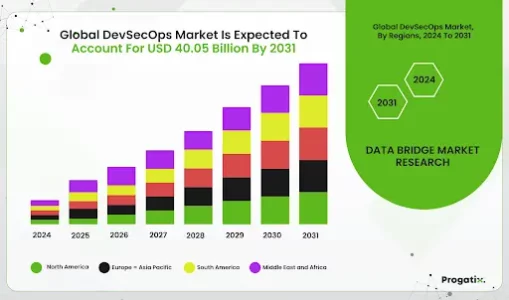
According to databridgemarketresearch, the global DevSecOps market was estimated at USD 4.48 billion in 2023 and is anticipated to reach USD 40.05 billion by 2031, with a CAGR of 31.5% during the forecast period of 2024 to 2031.
DevSecOps vs. DevOps
DevOps, a collaborative organizational model, unites software development and operations teams, helping IT departments meet opportunities and enhance efficiency. Organizations implementing a DevOps approach normally hire or train generalists rather than specialists because DevOps engineers will usually have awareness and context in both coding and system administration.
DevSecOps refers to the practice of integrating security during the software development life cycle (SDLC). It is based on a similar structure and evolved from the DevOps movement. This approach becomes important when operating in the cloud, where certain security protocols and requirements must be followed.
While targeting different business objectives, the two models can readily be confused due to their shared cultural similarities and emphasis on automation and cooperation. One interesting fact about DevOps vs. DevSecOps is that not all DevOps teams employ DevSecOps, but all DevOps teams use DevOps.
DevOps places immense value on team communication to enhance productivity and promote a culture of productive collaboration. The goal is to deconstruct silos and minimize barriers, usually resulting in a slower SDLC.
The goal of DevSecOps is to “shift security left” into active development rather than address it after the code is completed. By addressing security issues as soon as they arise, the aim is to support deployment security and compliance.
Enhance Your Skills with Our DevSecOps Guide!
Let's Connect
What are the components of DevSecOps?
Effective implementation of the DevSecOps practice comprises the following components:
-
Code analysis
Code analysis is the process of exploring an application’s source code for vulnerabilities while ensuring that it follows security best practices.
-
Change management
Software teams employ change management tools to track, manage, and report changes to software or requirements. This inhibits involuntary security vulnerabilities that may arise from a software change.
-
Compliance management
Software teams make sure that the software conforms to the regulatory requirements. For instance, developers can use AWS CloudHSM to validate compliance with security, privacy, and anti-tamper protocols such as HIPAA, FedRAMP, and PCI.
-
Threat modeling
DevSecOps teams examine security concerns that might arise before and after the application deployment to fix any identified issues and release the application with an updated version.
-
Security training
Security training comprises training software developers and operations teams with the up-to-date security guidelines. This way, the development and operations teams can make self-regulating security decisions during the building and deployment of the application.
How does DevSecOps work?
To implement DevSecOps, software teams first establish DevOps practices and continuous integration.
DevOps
DevOps is a development approach that links development and operations teams to work together more carefully, aiming to advance collaboration, communication, and visibility between the teams, making use of automation and tools. This leads to a fast software development process without compromising on flexibility or quality.
Continuous Integration
Continuous Integration (CI) and Continuous Delivery (CD) are modern software development methods that automate the build, testing, and deployment of code. This makes sure that small updates are rapidly and consistently integrated into an application. CI/CD tools help developers launch new versions of software and address issues as soon as the application is live. For instance, AWS CodePipeline is a well-known tool that automates deployment and management of applications.
DevSecOps
DevSecOps integrates security into the DevOps process by making security checks an endless part of the CI/CD pipeline. Rather than being a dispersed task managed by a different team at the end of development, security is everyone’s accountability from the outset. Developers and security teams collaborate to recognize risks and vulnerabilities before writing code, and operations teams keep monitoring the software for security concerns after it’s deployed. This approach allows businesses to deliver safe software rapidly while ensuring compliance.
DevSecOps Compared to DevOps
In standard DevOps, the focus is on getting applications to market fast, with security often managed independently at the end of the development cycle. Security teams usually test the application after it has been built, such as by setting up firewalls to check for vulnerabilities.
Security is interwoven throughout the entire development process with DevSecOps. To guarantee that security is embedded in the code itself, developers and security teams work together from the beginning. For example, developers develop code to reduce vulnerabilities, security teams install firewalls, and testers search for any potential safety risks in every program update or update, guaranteeing continuous security maintenance during the development process.
Significance of DevSecOps
DevSecOps aims to assist development teams address security concerns efficiently. It is a substitute to outdated software security practices that could not continue with strict timelines and rapid software updates. To realize the importance of DevSecOps, let us have a brief review at the software development process.
-
Software development lifecycle
The software development lifecycle (SDLC) is an organized process leading software teams to build high-quality applications. Software teams employ the SDLC to lessen costs and reduce errors, ensuring the software aligns with the project goals at all times. The software development life cycle takes software teams over these stages:
- Requirement analysis
- Planning
- Architectural design
- Software development
- Testing
- Deployment
DevSecOps in the SDLC
In traditional software development methods, security testing was an isolated process from the SDLC. The security team exposed security flaws only after they built the software. The DevSecOps framework enhances the SDLC by identifying vulnerabilities during the software development and delivery process.
Advantages of DevSecOps
Here are the number of benefits that come from practicing DevSecOps.
-
Identify Software Vulnerabilities Early
Software teams emphasize security controls throughout the whole development process. Instead of waiting until the software is finalized, they conduct checks at every stage. Software teams can identify security concerns at earlier stages and decrease the cost and time of fixing vulnerabilities. Consequently, users experience slight disruption and better security after the development of an application.
-
Decrease Time to Market
The software team, through DevSecOps, can automate security tests, lessen human errors, and prevent the security evaluation from holding up the development process.
-
Ensure Regulatory Compliance
Software teams utilize DevSecOps to comply with regulatory needs by adopting professional security practices and technologies. They recognize data protection and security requirements in the system. For instance, software teams employ AWS Security Hub to automate security checks alongside industry standards.
-
Develop a Security-Aware Setting
Software teams become more responsive to security best practices during application development. They are more proactive in recognizing potential security issues in the code, modules, or other technologies used to build the application.
-
Develop New Features Safely
The development, operation, and security teams communicate illegally via DevSecOps. They both have a similar understanding of software security and automate reporting and evaluation employing the same technologies. Everyone searches for strategies that improve customer value without compromising security.
Challenges related to DevSecOps Integration
Implementing DevSecOps can pose some challenges for organizations when they are getting started. Software development incorporates several technologies, including frameworks, languages, and architectures having their own unique way of operating and being developed. This can make it difficult for security teams to incessantly test and monitor them at the required speed.
Linking these development tools and techniques with inadequately configured security testing apparatuses can easily cause pipelines to become delicate. Brittle pipelines can halt when a part goes down or automations fail. This is a possible outcome with security teams failing to manage all the triggered events and the policies that rule them, which can be complex and time-taking.
To conclude, risks can occur anywhere alongside the pipeline, so it’s vital to implement security checks during the software development process to ensure that any new concerns apparent within the pipeline are spotted as soon as possible. It can, however, be challenging for teams to organize and manage the diversity of security checks needed due to the complex conditions listed above and inhibitions to transparency and priority that come from dispersed development and organizational complexities of DevSecOps.
Establishing a DevSecOps Culture
Making a change to a DevSecOps approach helps organizations address safety threats in real-time, but the change won’t occur suddenly. The right mindset is just as crucial as the right toolset in leaping. Here are five ways to organize yourself (and your team) to embrace DevSecOps:
-
Consider Security and security experts important assets
Acknowledge the bigger picture: Addressing a vulnerability that isn’t identified until much later will be considerably more challenging and expensive.
-
Work in small iterations
Make minimal iterations of your work. Delivering code in small segments will accelerate the process of identifying vulnerabilities.
-
Enable everyone to participate
Establish a custom where everyone can comment on and suggest progress on code and processes. Promising everyone on the team to stand up to changes pushes collaboration and makes everyone accountable for improving the process.
-
Stay prepared for an audit always
Create guidelines for gathering and updating compliance data while making sure that everyone on the team is mindful of how crucial compliance is.
-
Offer Training on security best practices
By offering comprehensive security standards and practical training, you can ensure that your development and operations staff have an understanding regarding secure development.
Boost Security Now with DevSecOps Best Practices!
Let's Connect
Best Practices of DevSecOps
Companies employ the following methods to support digital transformation with DevSecOps.
-
Shift left
Shift left refers to inspecting vulnerabilities in the beginning stages of software development, allowing software teams to avoid undetected security concerns during the application building process. For instance, developers create secure code in a DevSecOps process.
-
Shift right
Shift Right specifies the significance of emphasizing security after application deployment. Some vulnerabilities might emit prior security checks and become visible only when customers utilize the software.
-
Use automated security tools.
DevSecOps teams might demand to develop multiple revisions in a day, which require integration of security scanning tools into the CI/CD process, saving security evaluations from slowing down development.
-
Promote security awareness
Companies mark security awareness as an aspect of their core values when building software. Every team member who plays a part in application development must share the accountability of shielding software users from security threats.
-
Common DevSecOps tools
Software teams employ the following DevSecOps tools to measure, detect, and report security flaws during software development.
-
Static application security testing
Static application security testing (SAST) tools help analyze and find vulnerabilities in proprietary source code.
-
Software composition analysis
Software composition analysis (SCA) refers to the process of automating transparency into open-source software (OSS) use aiming for risk management, security, and license compliance.
-
Interactive application security testing
DevSecOps teams utilize interactive application security testing (IAST) tools to estimate the application’s potential susceptibilities in the production environment. IAST comprises special security monitors that function from within the application.
-
Dynamic application security testing
In order to validate the security of an application beyond the network, dynamic application security testing (DAST) technologies resemble hackers.
How can Progatix help with DevSecOps Integration?
By helping your company incorporate security into the software development lifecycle, a custom software development company can play a significant part in setting up DevSecOps. They begin with assessing your existing security and development practices to find any vulnerabilities and help develop a customized plan and strategy for integrating DevSecOps standards. By automating key processes and setting up DevOps procedures alongside pipelines for continuous integration (CI) and continuous delivery (CD) they ensure smooth collaboration between the development and operations teams. Furthermore, they may incorporate security testing straight into the CI/CD pipeline, leveraging automated technologies to find bugs prior to the code deployment. Assuring that security is a shared responsibility, they also help promote interaction between the operations, security, and development teams.
Conclusion
If you are concerned regarding the security of your software, contact Progatix, a custom software development company that employs best practices in security, such as role-based access control (RBAC), automated vulnerability scanning, and secure coding. We also employ automated compliance checks to ensure that industry standards are being observed. With ongoing assistance beyond the initial implementation, comprising incident response, security threat monitoring, and regular DevSecOps pipeline optimization, we help build secure software faster with reduced risks and improved compliance.


 Let's Discuss Your Tech Solutions
Let's Discuss Your Tech Solutions