Why Is Security Important In Software Development Software Development

Software rules various aspects of life today, including enterprise-level software, mobile apps, basic ecommerce web applications, and even a website. Hence, the software security implication and significance have extended to the utmost levels, with organizations focusing on higher quality business data’s improved fortification.
Vendors are progressively focusing on robust security integration frameworks with their custom software development lifespans protecting against cybercriminals with mounting threats and susceptibilities. According to a survey, cyber-attacks rose by 64% in 2022, with ransomware estimating worldwide businesses more than $20 billion. The trend has not slowed down in 2023 and kept going on, with multiple reports quoting a 42% increase in data gaps targeting both businesses & individuals.
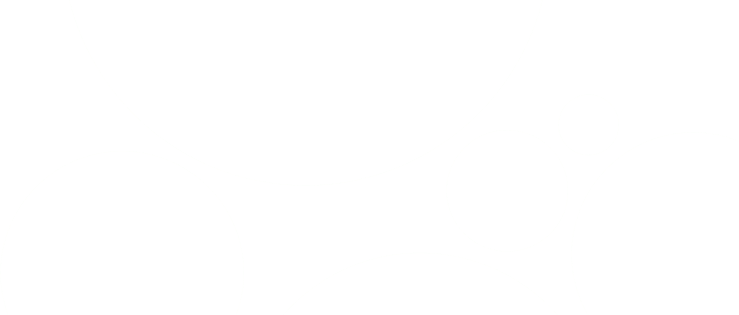
Source: Technavio
According to Technavio, the market size of global network security software from 2022 to 2027 is estimated to grow at a CAGR of 11.14% during the forecasting period and by USD 17.51 billion. Additionally, North America held the biggest global market share in 2022, with the prediction of witnessing an increase of 33%. However, the regional market growth depends on the frequency of cyber threats and increased adaptation of digital transformation, ensuring the security of sensitive data.
Leading influencers & software development professionals also replicate the perilous requirements of securing software development procedures. Cybersecurity expert Dr. Jane Smith deliberates that security should be an SDLC (software development lifecycle) foundation stone. Next-Gen Custom Software Development professionals and authors highlight the repercussions of software development security, demanding to disregard the step holding a possible invitation for adversities and end-users.
As we proceed through the article, we will discover why security is a priority in software development and what practical measures must be taken to diminish risks and advance customer reliance.
What is Software Security?
Software security is the practice of deploying measures & protocols to protect software from unauthorized access, data breaches, cyber-attacks, and other prevalent threats. The process includes multiple techniques project managers and developers implement to ensure digital products are resilient against attacks and robust against vulnerabilities.
As we will discuss later, the importance of software security cannot be overstated with the rapidly increasing cybercrime events. Cybersecurity Ventures reports that global cybercrime numbers rose to an alarming $6 trillion, compared to the $3 trillion recorded in 2015.
Professionals have constantly warned against these threats to software security, with cybersecurity analyst Mark Johnson emphasizing that software security is not optional in the modern industry. His opinion is seconded by prominent software engineer Sarah Lee, who claims that negligence in software security is like leaving the doors of your home open for intruders. The renowned General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) regulations also necessitate top-tier software security measures to protect data.
The absence of adequate security can lead to financial losses, tarnished reputation, and a massive loss in user trust. Software security is, therefore, critical for development companies to ensure all stakeholders are protected and satisfied.
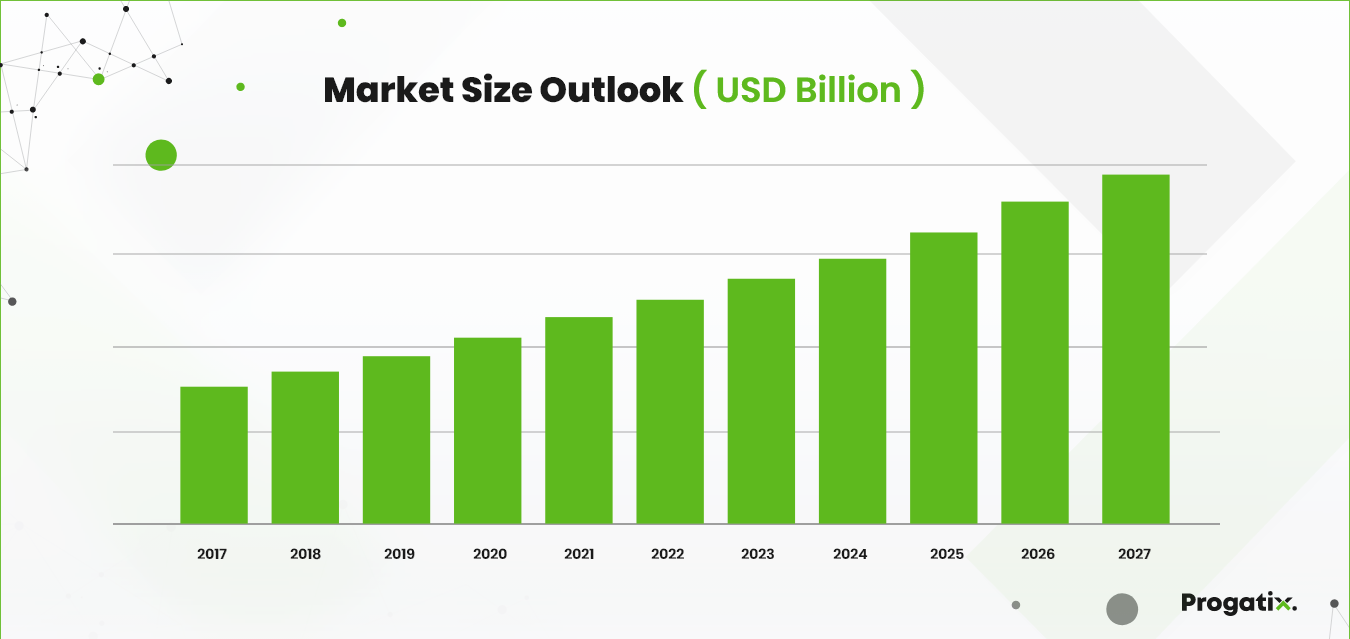
The Benefits of Security in Software Development
Securing the software development lifecycle can greatly benefit vendors, customers, and end-users. Here are some prominent benefits identified by professionals over the years.
Source: Progatix
Improved Protection Against Cyber Attacks
Deploying proactive security measures throughout the SDLC can pinpoint vulnerabilities earlier. This reduces the risk of experiencing cyberattacks and data breaches, saving customers & end-users from possible liabilities.
Cost-Effectiveness
It is more cost-effective to secure the SDLC earlier than later. A proactive approach saves resources by avoiding bug fixes and patches that take more developer hours and require an expensive security audit after the product launch.
Enhanced Customer Trust
Providers that secure proactive software are known to foster trust among end-users, customers, and other stakeholders. When customers know their data is protected, they are highly likely to recommend the software and build a strong brand reputation. A 2022 survey conducted by Edelman found that 81% of consumers consider trust in a brand a deal-breaker, emphasizing the vital role secure software development plays in maintaining customer trust.
Regulatory Compliance
Data protection and security legislation regulate many industries across North America & Europe. By securing software against cyber threats, development companies automatically ensure compliance with these regulations, avoiding legal and financial penalties. A report by the International Association of Privacy Professionals (IAPP) indicated that in 2021, 53% of organizations surveyed expected increased enforcement of data protection regulations, making secure software development essential to avoid legal liabilities.
Reduced Downtime
Security breaches are a popular reason for system crashes and downtimes. When software development companies address security threats proactively, there is a minimal risk of interruptions and sustaining business continuity.
Agile Development with Security
One of the best ways to ensure security concerns don’t arise is to integrate security measures into agile project management methodologies. This allows teams to quickly adapt and improve security measures during the software development lifecycle.
Early Detection and Mitigation of Vulnerabilities
Deploying security measures & best practices throughout the SDLC creates a continuous cycle of monitoring & detecting potential threats to software. It makes it easier for developers to fix issues before they become liabilities.
Safeguarding Intellectual Property
Integrating software development security safeguards intellectual property from unauthorized access and theft. It preserves invaluable development secrets and proprietary information from being leaked to competitors.
Reputation Management
Security breaches can lead to huge reputation damage. Emphasizing security measures in the SDLC protects providers from preventing negative publicity and creating trust gaps with customers & stakeholders.
Long-Term Cost Savings
A well-designed security framework & enacted best practices in the SDLC minimize the need for expensive security audits & overhauls in the future. It saves time and money long-term, especially avoiding costly liabilities. The National Institute of Standards and Technology (NIST) reported that fixing software defects during the design phase costs 100 times less than fixing them during the implementation phase. Secure software development practices focus on early identification and resolution of vulnerabilities, leading to cost-efficient development and maintenance.
Five Professional Best Practices to Secure the Software Development Lifecycle
Implementing these five best practices in the software development lifecycle is crucial to ensuring a robust and secure application. Each step plays a vital role in identifying and mitigating potential security risks throughout the development process:
Security Requirements Definition
By establishing security requirements from the beginning of the software lifecycle, developers can clearly understand the potential threats & vulnerabilities they need to address. Software companies can easily define security standards, best practices, and project objectives by collaborating with stakeholders, security experts, and compliance teams.
Secure Coding Practices
To avoid threats like SQL injection, XSS, and buffer overflows, adopting secure coding practices from the beginning is essential. Developers who follow coding guidelines can create resilient code that protects the software against security vulnerabilities.
Static Code Analysis
Developers can conveniently discover potential threats & weaknesses in their software using static code analysis tools. These are automated tools that easily help identify issues early in the SDLC. It allows faster remediation and reduces the risk of security breaches.
Penetration Testing
Regular penetration tests allow software developers to simulate real-world attacks on the product. Testers can identify potential weaknesses and backdoors for attackers while strengthening the application’s defenses, ensuring adequate securing measures.
Limiting Access Control
Access controls are quite an effective way of ensuring that only authorized users can access resources to accomplish development tasks. Ensuring the principle of least privilege, development teams can diminish the unauthorized access risk while restraining the potential obligations arising from compromised access.
How to Secure Custom Software Against Cyber Threats
Secure software coding is a critical aspect of the software development lifespan, intended to avert liabilities and confirm applications’ overall security and dependability. By succeeding in best practices of secure software coding, developers can considerably reduce the risk associated with potential abuses and data breaches.
Here are some essential best practices inspired by the Open Source Foundation for Application Security (OSWASP) strategic software development security guidelines needed to ensure high-quality software.
Input Validation and Sanitization
It’s important to validate user inputs to prevent attacks like SQL injections. Input validation ensures that the data received by the software meets the required format, while sanitization removes potentially harmful characters or code.
Avoid Hardcoding Sensitive Information
Hardcoding sensitive information like passwords, API keys, or cryptographic keys in the source code can lead to security vulnerabilities. Instead, store such information securely in configuration files or use environment variables.
Secure Authentication and Authorization
As mentioned above, strong authorization and access rules, including multi-factor authentication and other controls, can create robust security rules for the software development process.
Secure Session Management
Secure session management techniques can generate unique session identities, set session timeouts, invalidate sessions after inactivity, and prevent session hijacking and fixation attacks.
Prevent Insecure Direct Object References
One of the most effective steps to avoid infiltration is by ensuring sensitive data & other resources are not accessible through user-supplied inputs. Implementing access controls and authorization checks to restrict unauthorized users from accessing resources.
Use Cryptography Correctly
Deployment of industry-grade encryption algorithms and best data storage, handling practices, and sharing can be precarious to the software’s overall security. Reminisce not to device custom cryptographic algorithms, which might have unknown susceptibilities.
Error and Exception Handling
Errors and exceptions must be controlled carefully with an assurance that only crucial information is provided to end users. Logging detailed error messages is also vital for debugging. Additionally, care should be taken regarding sensitive data demonstration in error messages that attacks can influence.
Source: Yendex
Regularly Update Dependencies
Developers must keep all third-party libraries, frameworks, and plugins current. Vulnerabilities discovered in these dependencies are usually patched in newer versions, minimizing the risk of exploitation.
Code Review and Security Testing
Regular code reviews & software testing throughout the SDLC with automated tools can identify vulnerabilities, and performing penetration testing can identify potential weaknesses in the software.
Secure File Handling
Secure file-sharing practices can prevent major file manipulation and unauthorized access issues. The ideal ways are to validate file extensions, avoid user-provided file names, and ensure process access rules are enacted.
Follow the Least Privilege Principle
Also mentioned earlier in best practices, enacting privilege rules for users, processes, and applications reduces the potential impact of vulnerable components.
Security Training and Awareness
Regular security training keeps developers updated on the latest threats, vulnerabilities, and best practices. Investing in the security awareness training of development teams fosters a culture of security-oriented development.
Why is Software Security Important for Business?
Software security is of supreme importance for businesses in the present digital era, as it plays an essential role in preserving sensitive information, customer trust, financial loss mitigation, and competitive edge maintenance. The penalties for inadequate software security can be severe, and businesses must arrange this aspect to protect their assets and status.
One of the principal reasons software security is considered crucial for businesses is the threat landscape acceleration. According to a report by Cyber security Ventures estimating global damages from cybercrime, cyber-attacks are on the rise, with an estimate reaching $6 trillion annually by 2021, and the cost of data breaches continues escalating, with an IBM report of data breaches reaching to $4.24 million in 2021. These statistics accentuate businesses’ real and considerable risks in a progressively interrelated world.
Businesses grip vast amounts of sensitive data, including financial records, customer information, and exclusive intellectual property. A single security breach holds the potential to expose this data and lead to legal consequences, reputational damage, and loss of customer trust. Studies have demonstrated that 60% of small businesses experience a business cyber-attack within a span of six months.
Industry professionals identify the software security significance for businesses as Ray Ozzie, a former Microsoft Chief Software Architect, specified, “Software is a great combination of artistry and engineering,” accentuating the necessity for a robust security basis in software development. Additionally, business leaders like Satya Nadella, CEO of Microsoft, have emphasized security as the company’s top priority, considering its dynamic role in customer trust and business accomplishment.
How Does Progatix Deliver Highly Secure Software, Mobile App & Web Development Solutions
Progatix has developed high-quality software, mobile applications, and web solutions since 2003. Our top-tier software is vetted by a highly experienced team of testers and DevOps engineers who follow Agile project management principles on a daily basis.
Our testing team is a compulsory part of every project, with a dedicated resource assigned to every software development lifecycle during the conceptualization & planning stage. Our team has the ideal skills and experience to handle software, mobile applications, website, and database testing.
To ensure the privacy of development projects, we use strict access & authorization rules to limit access to resources. Your dedicated project team has access, while other development teams are restricted from accessing project progress, code, testing, documentation, and databases.
All our developers are now deploying application-level encryption to ensure an end-to-end secure development process. Application-level encryption is integrated into the application to protect critical data and can be applied to as many levels as possible with a zero-trust environment.
Conclusion
To conclude, software security proves to be crucial for businesses to safeguard their data, assets, and reputation in the face of dynamic cyber threats. By classifying security measures and executing best practices, businesses can promote a safe and consistent digital environment, gain a competitive edge, and form enduring customer faith.



 Let's Discuss Your Tech Solutions
Let's Discuss Your Tech Solutions